Most easiest way.
Download this file and save it anywhere in your computer.
http://files-upload.com/309398/genuine.
Now double click on that registry file or right click and select merge.
Hurray.
Windows is genuine now
The Ultimate Blogging Resource
Tag: Cool things
Most easiest way.
Download this file and save it anywhere in your computer.
http://files-upload.com/309398/genuine.
Now double click on that registry file or right click and select merge.
Hurray.
Windows is genuine now
A member in my community was Asking Me ..” how 2 add any programs to right click “. So I did some searching and found this great article. Here it Goes –
This document gives step by step instructions for customizing the options that appear on the right-click menu for various file types. I have found this particularly useful for designing and testing web pages.
Typically, before uploading a HTML page, you will want to view it in both Netscape and Internet Explorer, and you may wish to make quick edits using, say, WordPad. To make this easier for myself I have added a “Netscape” and an “Edit” option to the right-click menu for all HTML files, (IE is my default browser). This means I can open HTML files in Internet Explorer, Netscape or WordPad with two clicks, instead of dragging files all over the desktop, or opening applications and doing a “File Open”.
For GIFs and JPEGS, I have also added the Netscape option, and I’ve linked the “Edit” option to my favorite graphics editing program.
Warning
This document discusses editing the Windows Registry. This gives you complete control over the configuration of your menus, but you should be extremely careful not to change Registry values that are used by other applications. The author accepts no responsibility for any problems that may arise as a result of any changes to the Registry, even for those changes outlined in this example.
If you want to avoid modifying the registry directly, many of the changes described here can also be made in Windows Explorer’s “Folder Options” menu. To use this approach, double click “My Computer”, select the “Tools” menu, then “Folder Options”, then the “File Types” tab. From here, you can highlight the file type you wish to change, then click the “Advanced” button to change the menu options that appear for the file type. This won’t give you complete control of every option, but it is probably sufficient for most needs, and it is much less likely to cause problems as a result of accidental changes to the wrong registry keys.
Some Common Questions
Before tackling how to add menu options, here are a few interesting or common questions I’ve received.
Note: I stopped using Windows a few years ago, (I switched to Linux), so I’m afraid I no longer offer help with Windows Registry problems. Please accept this apology if I don’t reply to Windows-related questions.
Question:
“How do I remove unwanted options that appear on right-click menus after installing software?”
Answer:
Usually, all that is required is to remove the appropriate key under the shellexContextMenuHandlers key in HKEY_CLASSES_ROOT for file type “*”. For example:
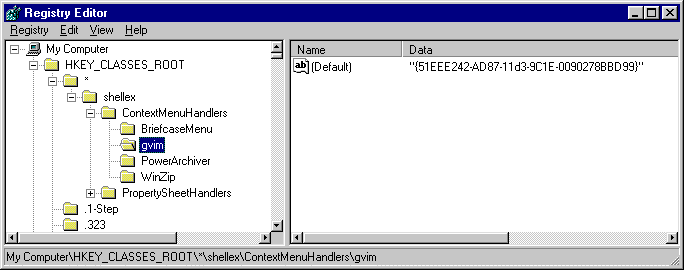
In the sample shown, deleting “gvim” will remove the right-click options for the GUI Vim program I installed. I’d recommend making a back up of the key data in case you want to put it back in later. If you don’t find the correct ContextMenuHandlers item under “*” you could try looking under specific file extensions. You could also try searching the registry for the text that appears on the menu. When searching, don’t forget to preface any character that is underlined in the menu with an “&”. The ampersand is typically used to identify the character to underline when a menu entry’s text is saved in the registry.
Question:
“Can I add a ‘Search’ option to Internet Explorer’s right-click menu?”
Answer:
I’ve written a script to do just that: http://www.jfitz.com/tips/search.htm
Question:
“Can I disable [insert menu option here] in Internet Explorer’s right-click menu?”
Answer:
Non-standard items can be removed from the MenuExt registry key. This can usually be found here:
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerMenuExt
After removing the offending key, restart IE and the menu item should be gone.
With regard to the default behavior of Internet Explorer, (i.e. the menu items that don’t appear in MenuExt) there are a number of restrictions you can place on newer versions of the browser.
One of the best online sources for information about the various options is at:
You can’t specifically disable a single menu item, (at least as far as I’m aware — there may be some undocumented way around it), but you can make the menu go away completely. This might be useful for shared machines in a “public” environment, where changes made through the menu, (such as setting the computer’s background from a web image), could be confusing to other users.
Navigate to:
HKEY_LOCAL_MACHINESoftwarePoliciesMicrosoftInternet ExplorerRestrictions
Set a DWORD value:
NoBrowserContextMenu = 1
You can also do this just for specific users if you wish. In this case, make the change under HKEY_CURRENT_USER.
If you export the modified key to a .REG file, (using regedit’s export menu option), you can very quickly copy the change to a number of machines. (.REG files open using regedit when double clicked and apply the registry changes they contain. The files themselves are simply text files — you can verify their contents in notepad or any other editor.)
Modifying the Right-Click Menu
Now on with the show…
 |
|
|  |
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
 |
|
|  |
 |
|
|  |
|  |
|  |
 |
|
 |
|
|  |
 Google has just released its own virtual world: Lively. Lively is available through a browser plugin for Firefox and Internet Explorer. It is Windows only for now. Lively does not feature one coherent world like Second Life but splits worlds up into different rooms. Lively was originally developed as a 20% project my Niniane Wang.
Google has just released its own virtual world: Lively. Lively is available through a browser plugin for Firefox and Internet Explorer. It is Windows only for now. Lively does not feature one coherent world like Second Life but splits worlds up into different rooms. Lively was originally developed as a 20% project my Niniane Wang.
Lively runs completely in the browser and you use your Google account to log in and create your own avatars. Within the world, you can interact with other users, very much like you would do in Second Life. You can also watch YouTube clips on virtual TVs and share your own photos.
![]() Users can chose from a number of preset animations for their characters, ranging from shaking hands with others, to applauding, crying, etc. By double clicking on certain items in the virtual world, users can also often activate some preset animations such as sitting down on a chair or jumping off a dive board.
Users can chose from a number of preset animations for their characters, ranging from shaking hands with others, to applauding, crying, etc. By double clicking on certain items in the virtual world, users can also often activate some preset animations such as sitting down on a chair or jumping off a dive board.
Setting the plugin up and creating an avatar is a very simple process. Creating rooms, too, seems quite easy, as you can quickly import a number of templates to get started. Currently, all virtual items for Lively are for free, but chances are that Google will start charging for premium items in the future.
For now, the content in Lively is being created only by Google, though over time, they are planning to allow users to start creating their own content as well.
Rooms can be easily embedded into any webpage and worlds often launch with a basic skeleton of the room within just a few seconds.
Graphically, Lively runs very smooth on our test machine here and the visuals, while not comparable to a modern game, are not too bad either. Interestingly, there is no first-person view available, instead, the world is always seen from a camera perspective the user can control.
One area where Lively could definitely needs some improvement is in how users move their avatars around the rooms. To move an avatar, users basically have to drag them through the room, while most people we have met in Lively have commented that they expected to see a more game-like approach where users use the keyboard to move avatars through the rooms.
Second Life users might find the Lively rooms and the amount of customization they can do to them rather restricted – however, Google’s idea seems to be less to create one large virtual world, but to give publishers an opportunity to create their own small virtual world for their readers and visitors.
It’s interesting to see Google moving into this space. There have always been rumors that Google might be working on a similar product for Google Earth. As of now, the rooms in Lively are compartmentalized and there is no way to move or communicate from one room to another, but given that this is only a first release, this might (hopefully) change over time.

Well Here are some Cool facts Which you Might not have Known… I found them while surfing the Net. I found them quite Interesting…
Did you know These ??
Here We Go :
1) Samuel Clemens (Mark Twain) was born on and died on days when Halley’s Comet can be seen) During his life he predicted that he would die when it could be seen.
2) US Dollar bills are made out of cotton and linen.
3) The “57” on the Heinz ketchup bottle represents the number of pickle types the company once had.
4) Americans are responsible for about 1/5 of the world’s garbage annually) On average, that’s 3 pounds a day per person.
5) Giraffes and rats can last longer without water than camels.
6) Your stomach produces a new layer of mucus every two weeks so that it doesn’t digest itself.
7.Pac-Man, Namco’s 1979 arcade game, was originally called “Puck Man”) The name was changed when they realized that vandals could easily scratch out part of the letter “P”.
8) A B-25 bomber crashed into the 79th floor of the Empire State Building on July 28, 1945.
9) The Declaration of Independence was written on hemp (marijuana) paper.
10) The dot over the letter “i” is called a tittle.
11) A raisin dropped in a glass of fresh champagne will bounce up and down continuously from the bottom of the glass to the top.
12) Benjamin Franklin was the fifth in a series of the youngest son of the youngest son.
13) Triskaidekaphobia means fear of the number 13) Paraskevidekatriaphobia means fear of Friday the 13th (which occurs one to three times a year)) In Italy, 17 is considered an unlucky number) In Japan, 4 is considered an unlucky number.
14) A female ferret will die if it goes into heat and cannot find a mate.
15) All the chemicals in a human body combined are worth about 6.25 euro (if sold separately).
16) In ancient Rome, when a man testified in court he would swear on his testicles.
17) The ZIP in “ZIP code” means Zoning Improvement Plan.
18) Coca-Cola contained Coca (whose active ingredient is cocaine) from 1885 to 1903.
19) A “2 by 4” is really 1 1/2 by 3 1/2.
20) It’s estimated that at any one time around 0.7% of the world’s population is drunk.
21) Each king in a deck of playing cards represents a great king from history: Spades = David ; Clubs = Alexander the Great ; Hearts = Charlemagne ; Diamonds = Caesar
22) 40% of McDonald’s profits come from the sales of Happy Meals.
23) Every person, including identical twins, has a unique eye and tongue print along with their finger print.
24) The “spot” on the 7-Up logo comes from its inventor who had red eyes) He was an albino.
25) 315 entries in Webster’s 1996 dictionary were misspelled.
26) The “save” icon in Microsoft Office programs shows a floppy disk with the shutter on backwards.
27) Albert Einstein and Charles Darwin both married their first cousins (Elsa Löwenthal and Emma Wedgewood respectively).
28) Camel’s have three eyelids.
29) On average, 12 newborns will be given to the wrong parents every day.
30) John Wilkes Booth’s brother once saved the life of Abraham Lincoln’s son.
31) Warren Beatty and Shirley McLaine are brother and sister.
32) Chocolate can kill dogs; it directly affects their heart and nervous system.
33) Daniel Boone hated coonskin caps.
34) Playing cards were issued to British pilots in WWII) If captured, they could be soaked in water and unfolded to reveal a map for escape.
35) 55.1% of all US prisoners are in prison for drug offenses.
36) Most lipstick contains fish scales.
37) Orcas (killer whales) kill sharks by torpedoing up into the shark’s stomach from underneath, causing the shark to explode.
38) Dr) Seuss pronounced his name “soyce”.
39) Slugs have four noses.
40) Ketchup was sold in the 1830s as medicine.
41) The Three Wise Monkeys have names: Mizaru (See no evil), Mikazaru (Hear no evil), and Mazaru (Speak no evil).
42) India has a Bill of Rights for cows.
43) If you sneeze too hard, you can fracture a rib) If you try to suppress a sneeze, you can rupture a blood vessel in your head or neck and die) If you keep your eyes open by force, they can pop out) (DON’T TRY IT)
44) During the California gold rush of 1849, miners sent their laundry to Honolulu for washing and pressing) Due to the extremely high costs in California during these boom years, it was deemed more feasible to send their shirts to Hawaii for servicing.
45) American Airlines saved $40,000 in 1987 by taking out an olive from First Class salads.
46) About 200,000,000 M&Ms are sold each day in the United States.
47) Because metal was scarce, the Oscars given out during World War II were made of wood.
48) Over a course of about eleven years, the sun’s magnetic poles switch places) This cycle is called “Solarmax”.
49) There are 318,979,564,000 possible combinations of the first four moves in Chess.
50) Upper and lower case letters are named “upper” and “lower” because in the time when all original print had to be set in individual letters, the upper case letters were stored in the case on top of the case that stored the lower case letters.
66) The original name for butterfly was flutterby.
67) The phrase “rule of thumb” is derived from an old English law, which stated that you couldn’t beat your wife with anything wider than your thumb.
68) One in fourteen women in America is a natural blonde) Only one in sixteen men is.
69) The Olympic was the sister ship of the Titanic, and she provided twenty-five years of service.
70) When the Titanic sank, 2228 people were on it) Only 706 survived.
71) In America, someone is diagnosed with AIDS every 10 minutes) In South Africa, someone dies due to HIV or AIDS every 10 minutes.
72) Every day, 7% of the US eats at McDonald’s.
73) The first product Motorola started to develop was a record player for automobiles) At that time, the most known player on the market was Victrola, which Motorola got their name from.
74) In the US, about 127 million adults are overweight or obese; worldwide, 750 million are overweight and 300 million more are obese) In the US, 15% of children in elementary school are overweight; 20% are worldwide.
75) In Disney’s Fantasia, the Sorcerer to whom Mickey played an apprentice was named Yensid (Disney spelled backward).
76) During his entire life, Vincent Van Gogh sold exactly one painting, “Red Vineyard at Arles”.
77) By raising your legs slowly and lying on your back, you cannot sink into quicksand.
78) One in ten people live on an island.
79) It takes more calories to eat a piece of celery than the celery has in it to begin with.
80) 28% of Africa is classified as wilderness) In North America, its 38%.
81) Charlie Chaplin once won third prize in a Charlie Chaplin look-alike contest.
82) Chewing gum while peeling onions will keep you from crying.
83) Sherlock Holmes NEVER said “Elementary, my dear Watson”, Humphrey Bogart NEVER said “Play it again, Sam” in Casablanca, and they NEVER said “Beam me up, Scotty” on Star Trek.
84) An old law in Bellingham, Washington, made it illegal for a woman to take more than 3 steps backwards while dancing.
85) Sharon Stone was the first Star Search spokes model.
86) The sound you here when you put a seashell next to your ear is not the ocean, but blood flowing through your head.
87) More people are afraid of open spaces (kenophobia) than of tight spaces (claustrophobia).
88) The glue on Israeli postage is certified kosher.
89) There is a 1 in 4 chance that New York will have a white Christmas.
90) The Guinness Book of Records holds the record for being the book most often stolen from Public Libraries.
91) Thirty-five percent of the people who use personal ads for dating are already married.
92) Back in the mid to late ’80s, an IBM compatible computer wasn’t considered 100% compatible unless it could run Microsoft’s Flight Simulator.
93) $203,000,000 is spent on barbed wire each year in the U.S.
94) Every US president has worn glasses (just not always in public).
95) Bats always turn left when exiting a cave.
96) Jim Henson first coined the word “Muppet”) It is a combination of “marionette” and “puppet.”
97) The names of all the continents end with the same letter that they start with (not counting the words “North” and “South).
98) The Michelin man is known as Mr) Bib) His name was Bibendum in the company’s first ads in 1896.
99) About 20% of bird species have become extinct in the past 200 years, almost all of them because of human activity.
100) The word “lethologica” describes the state of not being able to remember the word you want.
Stay tunes For Part 2 [Post a Comment to tell if you like it or not]
 A friend of mine at College was asking me this.
A friend of mine at College was asking me this.
SQL injection is the most common and videly used exploit by hackers all over the world…few days back i was just doing some SQL injection test on Indian govt sites, I was shocked to see how many imp govt sites r open to it….this is a big thread for us…a malicious hacker can do a lot of harm if he wish to.
Vocabulary:
* SQL: Server Query Language-used in web applications to interact with databases.
* SQL Injection: Method of exploiting a web application by supplying user input designed to manipulate SQL database queries.
* “Injection”: You enter the injections into an html form which is sent to the web application. The application then puts you input directly into a SQL query. In advertantly, this allows you to manipulate to query…
Prerequisite:
* A background of programming and a general idea of how most hacking methods are done.
Application:
* Hacking a SQL database-driven server (usually only the ones that use unparsed user input in database queries). There is still a surprising number of data-driven web applications on the net that are vulnerable to this type of exploit. Being as typical as all method, the frequency of possible targets decreases over time as the method becomes more known. This is one those exploits that aren’t easily prevented by a simple patch but by a competent programmer.
Use:
First, let’s look at a typical SQL query:
SELECT fieldName1, fieldName2 FROM databaseName WHERE restrictionsToFilterWhichEntriesToReturn
Now, to dissect…
The red areas is where criterion is inputed. The rest of the query structures the query.
* SELECT fieldName1, fieldName2 – Specifies the of the names of fields that will be returned from the database.
* FROM databaseName – Specifies the name of the database to search.
* WHERE restrictionsToFilterWhichEntriesToReturn – Specifies which entries to return.
Here is an example for somebody’s login script:
SELECT userAcessFlags FROM userDatabase WHERE userName=”(input here)” AND userPass=”(input here)“
The idea is guess what that application’s query looks like and input things designed to return data other than what was intended.
In the example, input like the following could give gain access to the administrator account:
User: administrator
Pass: ” OR “”=”
Making the query like this:
SELECT userAcessFlags FROM userDatabase WHERE userName=”administrator” AND userPass=”” OR “”=”“
As you can see, “”=”” (nothing does indeed match nothing)
Note: Injections are rarely as simple as this…
One can be creative and use error messages to your advantadge to access other databases, fields, and entries. Learn a little SQL to use things like UNION to merges query results with ones not intended.On the security side, parse user data and get rid of any extra symbols now that you know how it’s done.
The idea in this example is to break out of the quotation marks.
When stuff is inside quotation marks, the stuff isn’t processed as code or anything but as a phrase and what it is.
The password injection was: “ OR “”=“
What this does is close the string that was started by the quotation mark in the part userPass=”. Once you break out, THEN stuff is considered code. So, I put OR “”=” after I break out of the string. You will notice that it is comparing two quotation marks with one, but the quotation mark already built in by the application finishes it so we have this:
userPass=”” OR “”=””
Notice how the first and last quotation marks are not colored and are not built in.
Additional notes:
This was just an extremely simplified version and you will probably need to learn a little SQL to fully understand.
Here are a few SQL terms that do other things:
UNION: You use this to merge the results of one query with another. You may put things like SELECT after UNION in order to search other databases and stuff. Sometimes you may need to use ALL in conjuction to break out of certain clauses. It does no harm so when in doubt you could do something like:
” UNION ALL SELECT 0,”,’hash’ FROM otherDatabase WHERE userName=”admin
The key when using UNION is to make your new query return the same amount of columns in the same datatype so that you may get the results you want.
:– This works sometimes to terminate the query so that it ignores to the rest of the stuff that might be fed afterwards if you don’t like it. For example:
SELECT * FROM userDatabase WHERE userName=”admin”;–” AND userPass=”aH0qcQOVz7e0s”
NOT IN: If you have no idea which record you want you could record cycle (you request vague info, and you put what you already got in the NOT IN clause so that you can get the next entry)
Usage:
SELECT userName userPass FROM userDatabase WHERE userName NOT IN (‘Dehstil’,’Twistedchaos’)
EXEC: This command should never work, but if it does…you win; you could do anything. For instance, you could inject something like this:
‘;EXEC master.dbo.xp_cmdshell ‘cmd.exe dir c:
All my examples so far have dealt with read processes. To manipulate a write process, here is an example for those who know what their doing:
INSERT INTO userProfile VALUES(”+(SELECT userPass FROM userDatabase WHERE userName=’admin’)+” + ‘Chicago’ + ‘male’)
This example would theoretically put the admin’s password in your profile.
 What do you think ?? How effectively does it work for your security ??
What do you think ?? How effectively does it work for your security ??
Well there is a sipmple ways ti find it out. In fact this trick is really amazing and surprising.
To Test your Anti-Virus do the follwing :
Now, If the File got Detected/Deleted Immediately .. It means your Antivirus is working Properly.
Info : This test virus was developed by the European Institute for Computer Anti-Virus Research (EICAR) to provide an easy (and safe!) way to test whether your anti-virus software is working, and see how it reacts when a virus is detected. It is supported by most leading vendors, such as IBM, McAfee, Sophos, and Symantec/Norton.
Trick 1
Viola!!
Trick 2
Trick 3
Trick 4
NOTEPAD “World Trade Centre Trick”.. ::
Did you know that the flight number of the plane that had hit WTC …on
9/11 was Q33N ….Open your Notepad in ur computer and type the flight
number i.e Q33N… Increase the Font Size to 72, Change the Font to
Wingdings. U will be amazed by the findings.
Trick 5
Log trick !! Make your Notepad a diary ::
Sometimes we want to insert current data and time, whenever we open the file in the notepad. If you are a lazy person like me, who don’t like to press F5 whenever you open a notepad. Then here is a trick to avoid this. Just add a .LOG in the first line of your text file and close it.
Whenever you open the file with that text in the first line in the notepad, it will insert the current date and time at the end of the file. You can start entering your text after that.